Being your own CA and Issuing OpenSSL Certs
Be your own Certificate Authority (CA) and issue your own signed certificates to use for encrypted communications

Download the OpenSSL installer for Windows, use the full version not the Light version https://slproweb.com/products/Win32OpenSSL.html
After installing you want to add openssl to your system PATH. Search for Environment Variables. Add the variable OPENSSL_CONF with the value C:\Program Files\OpenSSL-Win64\bin\openssl.cfg and add C:\Program Files\OpenSSL-Win64\bin to the Path.
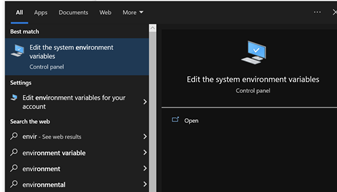
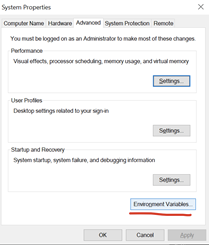
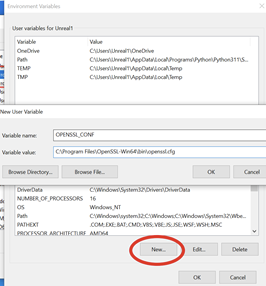
Steps for editing system environment variables
You should be able to run OpenSSL in console
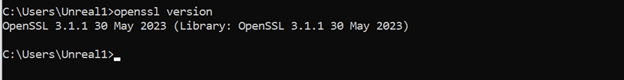
In this case we will make a new directory called “certs” to keep all the files together mkdir certs
We can cd into the certs directory and run the command : openssl genrsa -des3 -out myCA.key 2048
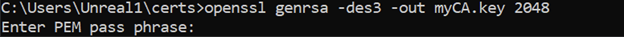
This allows us to secure the key with a password. You can enter anything you like.
We will now generate a root certificate: openssl req -x509 -new -nodes -key myCA.key -sha256 -days 2000 -out myCA.pem
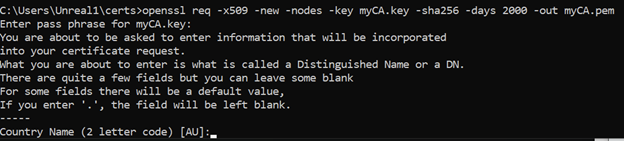
You will be prompted to enter answers to several questions, they won’t affect the cert as they are just viewed for ease of use.
In your certs folder you will see the .key and .pem files

We want to add them to the system, so we can search “Manage computer certificates"
Navigate to Trusted Root Certification Authorities > Right-click on “Certificates” > “All Tasks” > Import
When selecting the file to import add the .pem that was generated. Don’t forget to allow for all file types.
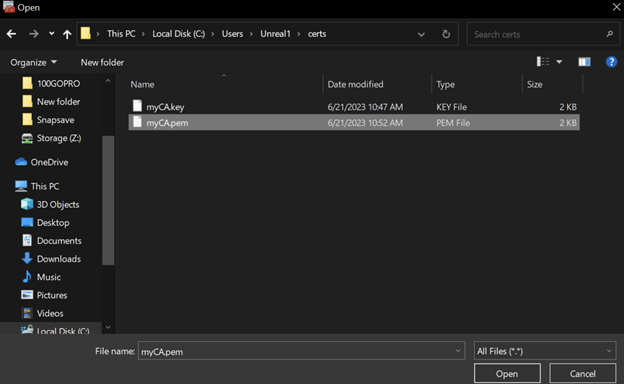
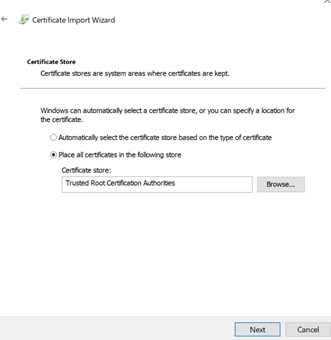
Leave the certificate store as “Trusted Root Certification Authorities”
Now we can act as a CA and create our own signed keys, we can create a private key per site like in this example openssl genrsa -out mydomain.local.test.key 2048
Then we create a CSR : openssl req -new -key mydomain.local.test.key -out mydomain.local.test.csr
You will be asked the same description questions, but they do not affect your key at all and are for informational purposes. However, you will be prompted with a challenge password, this will be used for revocation purposes
We can create an extension config file to configure the subject alternative name (SAN) for the cert. I’ll just make a mfc.local.test.ext with the following code:
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = mydomain.local.testNow we can run the command to create the certificate : openssl x509 -req -in mydomain.local.test.csr -CA myCA.pem -CAkey myCA.key -CAcreateserial -out mydomain.local.test.crt -days 825 -sha256 -extfile mydomain.local.test.ext
You will be prompted for the password you entered for the CA key in the beginning and should have a folder that looks like this. The serial number file (.slr) is to ensure that each signed certificate has a unique serial number. When the CA signs a new certificate, OpenSSL reads the serial number from the .srl file, increments it, and writes the updated value back to the same file. This way, the CA can keep track of the serial numbers it has



